World readable files strike again. Check what that user was up to, and use it to log into flag08 account.
To do this level, log in as the level08 account with the password level08. Files for this level can be found in /home/flag08.
There is no source code available for this level
刚开始打开目录的时候我是懵的,里面只有一个root权限建立的capture.pcap文件。VIM打开看是乱码,用strings capture.pcap隐约能看到几个password的ASCII字符。
Google了一下,发现pcap是wireshark的记录文件后缀,用tcpdump也可以生成和阅读。可是目标环境中没有wireshark,尝试用tcpdump打开文件看看。
$ tcpdump -r capture.pcap > ~/readable.txt
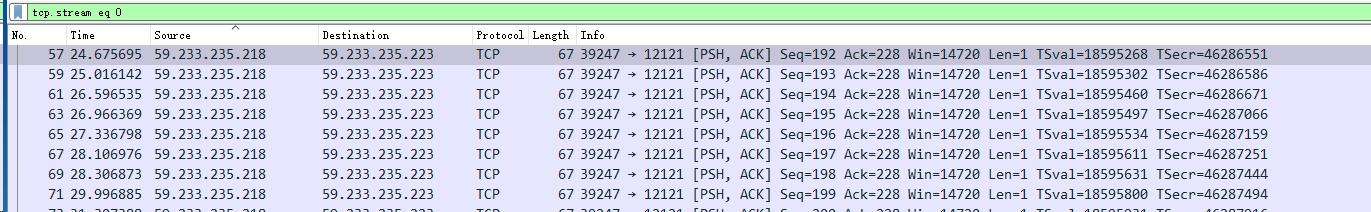
打开一看,全是类似如下格式的报文:
21:23:12.267566 IP 59.233.235.218.39247 > 59.233.235.223.12121: Flags [S], seq 2635601089, win 14600, options [mss 1460,sackOK,TS val 18592800 ecr 0,nop,wscale 7], length 0
21:23:12.267694 IP 59.233.235.223.12121 > 59.233.235.218.39247: Flags [S.], seq 3131636289, ack 2635601090, win 14480, options [mss 1460,sackOK,TS val 46280417 ecr 18592800,nop,wscale 5], length 0连之前找到的password几个字符都没了,估计是tcpdump显示的信息不完整。于是只能先把东西传出来,用正经的wireshark来读。
$ scp /home/flag08/capture.pcap [email protected]:/home/liuz
用wireshark打开,看起来依然是一条条报文而已。
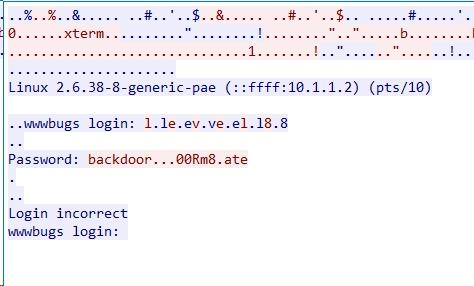
不过,根据大神的指示,原来wireshark还有直接看信息流这么高级的功能(分析-追踪流-TCP流)。
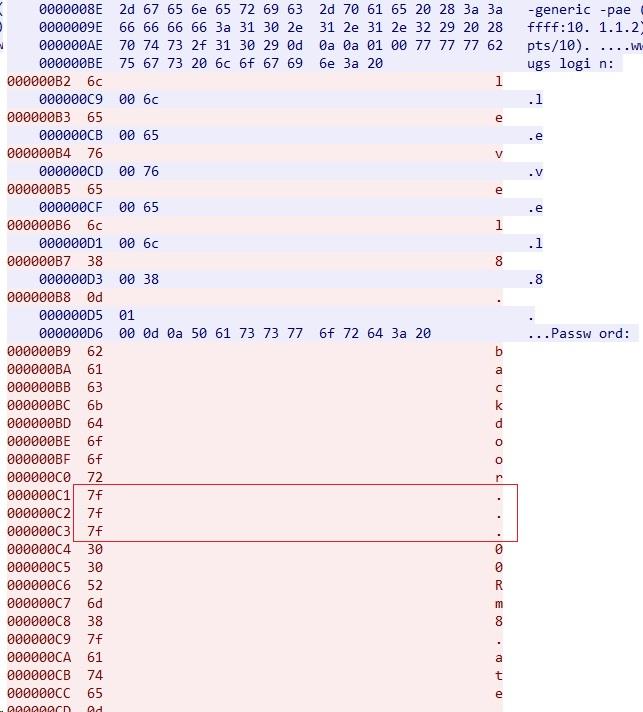
这里就能看到strings命令看到的password字符,然而不知道啥意思。大神又说,要有光,于是有了光(数据显示为-HEX转储)。
据说那几个7f对应ASCII是.,也就是退格键。所以拼凑起来的密码就是backd00Rmate。
用这个密码登录flag08后,再getflag,果然……
test for comment
another test for comment
3rd test
@wellsleeplz 嘿嘿
this is the comment from the US
this is comment from linux.